How to manage malicious traffic coming from the Amazon Web Services (AWS) network
In recent times, website security has become a pressing concern, with malicious activities and cyber threats on the rise. One recurring issue faced by many website owners is the influx of malicious traffic originating from the Amazon Web Services (AWS) network. This disruptive traffic, often in the form of bots and automated scripts, can significantly impact a website’s performance, security, and overall user experience.
Understanding the gravity of this situation, it becomes imperative for website administrators and owners to implement effective strategies to manage and mitigate the impact of such malicious traffic. In this blog post, we will delve into several actionable steps that can be taken to address and manage malicious traffic originating from AWS:
- Traffic Analysis and Identification: The first step is to accurately identify and analyze the malicious traffic affecting your website. Utilize web analytics tools and server logs to pinpoint the source, patterns, and characteristics of the traffic. Identify AWS IP ranges or specific instances causing the issue.
- Implement Firewall Rules: Configure your website’s firewall or security settings to block or restrict traffic from AWS IP ranges associated with the malicious activity. Use tools like IP blacklisting to filter out unwanted traffic.
- Utilize Rate Limiting and CAPTCHA: Implement rate-limiting techniques to restrict the number of requests from specific IP addresses. Integrate CAPTCHA challenges or other verification methods to differentiate human users from bots.
- Employ Content Delivery Network (CDN): Utilize a reliable CDN service to distribute your website’s content across various servers globally. CDNs often include security features that help mitigate malicious traffic and ensure faster, more secure content delivery.
- Regularly Update Security Measures: Stay vigilant and proactive by continuously updating security measures, software, and plugins on your website. Patch any vulnerabilities that might be exploited by malicious traffic.
- Report Abuse to AWS: If you have identified specific AWS resources contributing to the malicious traffic, report abuse to Amazon. Provide detailed information and evidence to support your claim.
- Consider Professional Assistance: In severe cases where the malicious traffic persists despite your efforts, consider seeking professional assistance from cybersecurity experts or consulting AWS support services.
Managing malicious traffic originating from AWS demands a proactive and multifaceted approach. By implementing these strategies and staying vigilant, website administrators can better protect their websites from the adverse effects of such unwanted traffic.
Remember, securing a website is an ongoing process. Regular monitoring, analysis, and adaptation of security measures are crucial to safeguard against evolving threats.
Stay informed, stay proactive, and safeguard your website against malicious traffic from the AWS network. Your website’s security is paramount, and taking proactive measures is key to protecting your online presence.
CASE STUDY :
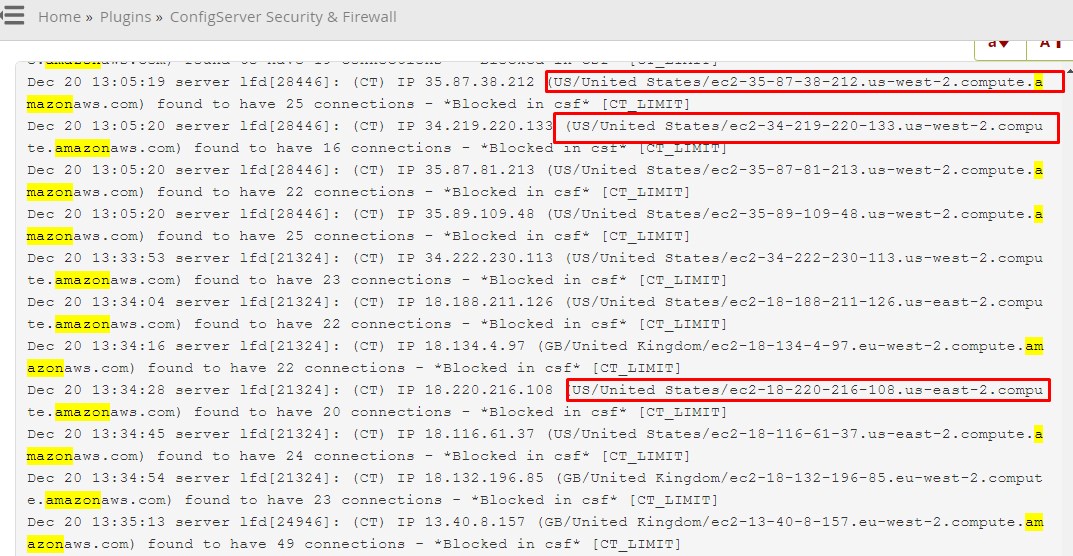
Over the past few months, our client website has been experiencing a substantial volume of inbound traffic from Amazon host servers, which appeared to be identified as malicious bot activity. Upon further investigation and analysis of our web traffic logs, it has become evident that this influx of automated and suspicious traffic is significantly affecting the performance and security of our website.
The malicious bot traffic has been detrimental to our website’s normal operation, causing undue strain on our server resources, disrupting the user experience, and potentially compromising the integrity and security of our platform.
We have implemented various security measures and filtering techniques to mitigate the impact of this malicious activity. However, the persistent nature and volume of this bot traffic originating from Amazon host servers continue to pose a severe threat to the stability and functionality of our website.
As a responsible web service provider, we highly value the security and integrity of our online platform.
Often, we encounter instances of malicious traffic originating from the Amazon Web Services (AWS) network. Attackers frequently attempt to establish connections to cPanel or WordPress. If you notice such incursions on your server, considering the temporary blockage of AWS traffic might be a prudent step.
To implement this, you can obtain the AWS IPs and append them to the CSF csf.deny file. The command below allows you to download the JSON file, which is the sole format provided by Amazon:
# wget https://ip-ranges.amazonaws.com/ip-ranges.json
Now for extracting the IP prefixes from the ip-ranges.json file. use the command:
grep ip_prefix ip-ranges.json | awk '{print $2}' | tr -d ',"'
Output:
root@web [/temp4]# grep ip_prefix ip-ranges.json | awk '{print $2}' | tr -d \",
3.2.34.0/26
3.5.140.0/22
13.34.37.64/27
13.34.65.64/27
13.34.66.0/27
13.34.78.160/27
13.34.103.96/27
15.230.15.29/32
15.230.15.76/31
15.230.221.0/24
35.180.0.0/16
51.85.0.0/16
52.93.153.170/32
52.93.178.234/32
52.93.244.0/24
52.94.76.0/22
52.95.36.0/22
......
This command uses grep to filter lines containing “ip_prefix” from the ip-ranges.json file. Then, awk extracts the second column (which contains the IP prefixes), and tr removes any occurrences of double quotes and commas to ensure the output consists solely of the IP prefixes.
